Let’s use Python regex to validate an IP address. Let’s go!
Regex is short for “regular expression”. A regular expression is a pattern, defined in Python code, that will be compared to a target string for matches. In the following example, we will write some code to detect and validate IP addresses using regular expressions:
import re
ip ="255.255.255.0"
validip = re.match(r"^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])$",ip)
print(validip.group())
#output
#255.255.255.0Let’s explain what is happening here:
- First we import the regular expression module re.
- We define the ip address value to be tested for a match ip.
- We use a regular expression defined as the pattern parameter of the re.match() function. This complex looking regular expression pattern will only match valid IPv4 IP addresses.
- We print the matching group if it exists.
If the above executes, you should see the matching IP address printed to the screen. Let’s do another case, this time let’s try a few more examples, even invalid ones:
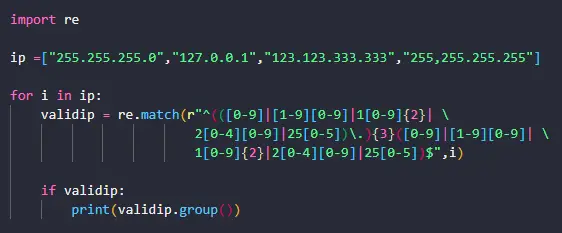
import re
ip =["255.255.255.0","127.0.0.1","123.123.333.333","255,255.255.255"]
for i in ip:
validip = re.match(r"^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])$",i)
if validip:
print(validip.group())
#output
#255.255.255.0
#127.0.0.1
All the same steps except that we are seeking to match the elements of a list this time. The elements of the list ip contain both valid and invalid IP addresses. The regex should only match valid IP addresses for IPv4 type addresses. So we try to match each element in a loop against our regex pattern defined in the re.match() function. This time we only get two valid IP addresses.
We can do something similar to validate IPv6 type IP addresses. See the code below:
import re
ipv6 = ["2001:db8:3333:4444:5555:6666:7777:8888","2001:db8:3333:4444:CCCC:DDDD:EEEE:FFFF","2001:db8:3333:4444:CCCC:DDDD:EEEE:ZZZZ","192:168:100:100"]
for i in ipv6:
validip = re.match(r'^(?:(?:[0-9A-Fa-f]{1,4}:){6}(?:[0-9A-Fa-f]{1,4}:[0-9A-Fa-f]{1,4}| \
(?:(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5]))| \
::(?:[0-9A-Fa-f]{1,4}:){5}(?:[0-9A-Fa-f]{1,4}:[0-9A-Fa-f]{1,4}|(?:(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]| \
25[0-5])\\.){3}(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5]))| \
(?:[0-9A-Fa-f]{1,4})?::(?:[0-9A-Fa-f]{1,4}:){4}(?:[0-9A-Fa-f]{1,4}:[0-9A-Fa-f]{1,4} \
|(?:(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}(?:[0-9]|[1-9][0-9]|1[0-9]{2}| \
2[0-4][0-9]|25[0-5]))|(?:[0-9A-Fa-f]{1,4}:[0-9A-Fa-f]{1,4})?::(?:[0-9A-Fa-f]{1,4}:){3}(?:[0-9A-Fa-f]{1,4}:[0-9A-Fa-f]{1,4}| \
(?:(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5]))| \
(?:(?:[0-9A-Fa-f]{1,4}:){,2}[0-9A-Fa-f]{1,4})?::(?:[0-9A-Fa-f]{1,4}:){2}(?:[0-9A-Fa-f]{1,4}:[0-9A-Fa-f]{1,4}| \
(?:(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5]))| \
(?:(?:[0-9A-Fa-f]{1,4}:){,3}[0-9A-Fa-f]{1,4})?::[0-9A-Fa-f]{1,4}:(?:[0-9A-Fa-f]{1,4}:[0-9A-Fa-f]{1,4}|(?:(?:[0-9]| \
[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5]))| \
(?:(?:[0-9A-Fa-f]{1,4}:){,4}[0-9A-Fa-f]{1,4})?::(?:[0-9A-Fa-f]{1,4}:[0-9A-Fa-f]{1,4}|(?:(?:[0-9]|[1-9][0-9]| \
1[0-9]{2}|2[0-4][0-9]|25[0-5])\\.){3}(?:[0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5]))| \
(?:(?:[0-9A-Fa-f]{1,4}:){,5}[0-9A-Fa-f]{1,4})?::[0-9A-Fa-f]{1,4}|(?:(?:[0-9A-Fa-f]{1,4}:){,6}[0-9A-Fa-f]{1,4})?::)$',i)
if validip:
print(validip.group())
#output
#2001:db8:3333:4444:5555:6666:7777:8888
#2001:db8:3333:4444:CCCC:DDDD:EEEE:FFFFSo validating IPv6 addresses is a bit more tricky. Because the ip address is 128-bits as opposed to the 32-bit IPv4 address, there are more possibilities and consequently the pattern needs to be adjusted to handle more eventualities. This is why it is so much longer.
Neat right? Thanks for reading! 🔥🔥🔥✨✨

Are you worried about your child’s online safety or your employees’ productivity? Do you wonder what they’re accessing on their devices? SentryPC is here to address these concerns. This all-in-one, cloud-based software provides robust activity monitoring, content filtering, and time management, making it ideal for both parental control and employee monitoring. Embrace peace of mind and enhanced efficiency with SentryPC, the proactive solution to your digital monitoring needs. CLICK HERE to get started.

