Let’s do a Python Blowfish Encryption example. Let’s go! 🔥 🔥
Blowfish is a symmetric-key block cipher algorithm designed for fast encryption and decryption of data. It’s particularly notable for its simplicity and speed. In Python, Blowfish encryption can be implemented using the cryptography library, which provides a secure and user-friendly way to handle cryptographic operations. You can install the cryptography library using the pip install cryptography or pip3 install cryptography command at the terminal. Once you do that, you’re ready to rock!
Here’s a basic example of Blowfish encryption in Python, followed by a line-by-line explanation:
from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modes
from cryptography.hazmat.backends import default_backend
from cryptography.hazmat.primitives import padding
from os import urandom
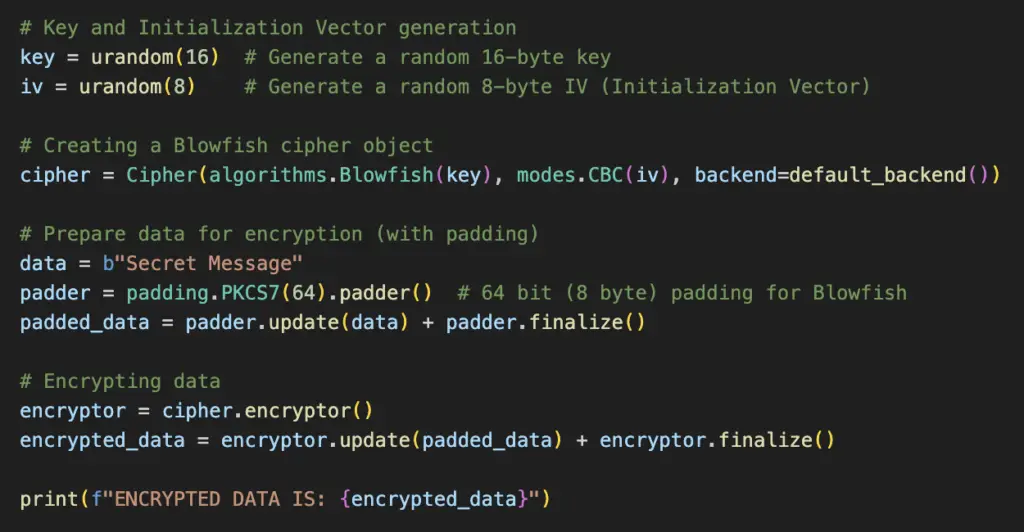
# Key and Initialization Vector generation
key = urandom(16) # Generate a random 16-byte key
iv = urandom(8) # Generate a random 8-byte IV (Initialization Vector)
# Creating a Blowfish cipher object
cipher = Cipher(algorithms.Blowfish(key), modes.CBC(iv), backend=default_backend())
# Prepare data for encryption (with padding)
data = b"Secret Message"
padder = padding.PKCS7(64).padder() # 64 bit (8 byte) padding for Blowfish
padded_data = padder.update(data) + padder.finalize()
# Encrypting data
encryptor = cipher.encryptor()
encrypted_data = encryptor.update(padded_data) + encryptor.finalize()
print(f"ENCRYPTED DATA IS: {encrypted_data}")
# Decrypting data
decryptor = cipher.decryptor()
decrypted_padded_data = decryptor.update(encrypted_data) + decryptor.finalize()
# Remove padding after decryption
unpadder = padding.PKCS7(64).unpadder()
decrypted_data = unpadder.update(decrypted_padded_data) + unpadder.finalize()
print(f"DECRYPTED DATA IS: {decrypted_data}")
#output
#ENCRYPTED DATA IS: b'\xc4\xf6\xad\xa3n\xc6\xc3W\xb9\xcb,=\xf1\xd9\xaa\xa6'
#DECRYPTED DATA IS: b'Secret Message'Let’s explain what’s happening here:
- Import Required Modules:
- Import
Cipher,algorithms,modesfromcryptography.hazmat.primitives.ciphersfor cryptographic operations. - Import
default_backendfromcryptography.hazmat.backendsfor cryptographic backend support. - Import
paddingfromcryptography.hazmat.primitivesfor data padding. - Import
urandomfromosfor generating random bytes (keys and IVs).
- Import
- Key and IV Generation:
key = urandom(16)generates a random 16-byte key.iv = urandom(8)generates a random 8-byte Initialization Vector.
- Create Blowfish Cipher Object:
cipher = Cipher(algorithms.Blowfish(key), modes.CBC(iv), backend=default_backend())creates a Blowfish cipher object in Cipher Block Chaining (CBC) mode.
- Prepare Data for Encryption (With Padding):
data = b"Secret Message"sets the plaintext message.padder = padding.PKCS7(64).padder()creates a padding object for 64-bit (8-byte) blocks.padded_data = padder.update(data) + padder.finalize()pads the plaintext to a multiple of the block size.
- Encrypting Data:
encryptor = cipher.encryptor()creates an encryptor instance from the cipher.encrypted_data = encryptor.update(padded_data) + encryptor.finalize()encrypts the padded data.
- Decrypting Data:
decryptor = cipher.decryptor()creates a decryptor instance from the cipher.decrypted_padded_data = decryptor.update(encrypted_data) + decryptor.finalize()decrypts the data, still containing padding.
- Remove Padding After Decryption:
unpadder = padding.PKCS7(64).unpadder()creates an unpadder for 64-bit blocks.decrypted_data = unpadder.update(decrypted_padded_data) + unpadder.finalize()removes the padding from decrypted data, yielding the original plaintext.
That does it for our Python Blowfish Encryption Example. Happy coding!👌🏻👌🏻👌🏻
